
Shift Process Of The AES S-Box. (A) Example Of The Round Key. (B) S-Box... | Download Scientific Diagram
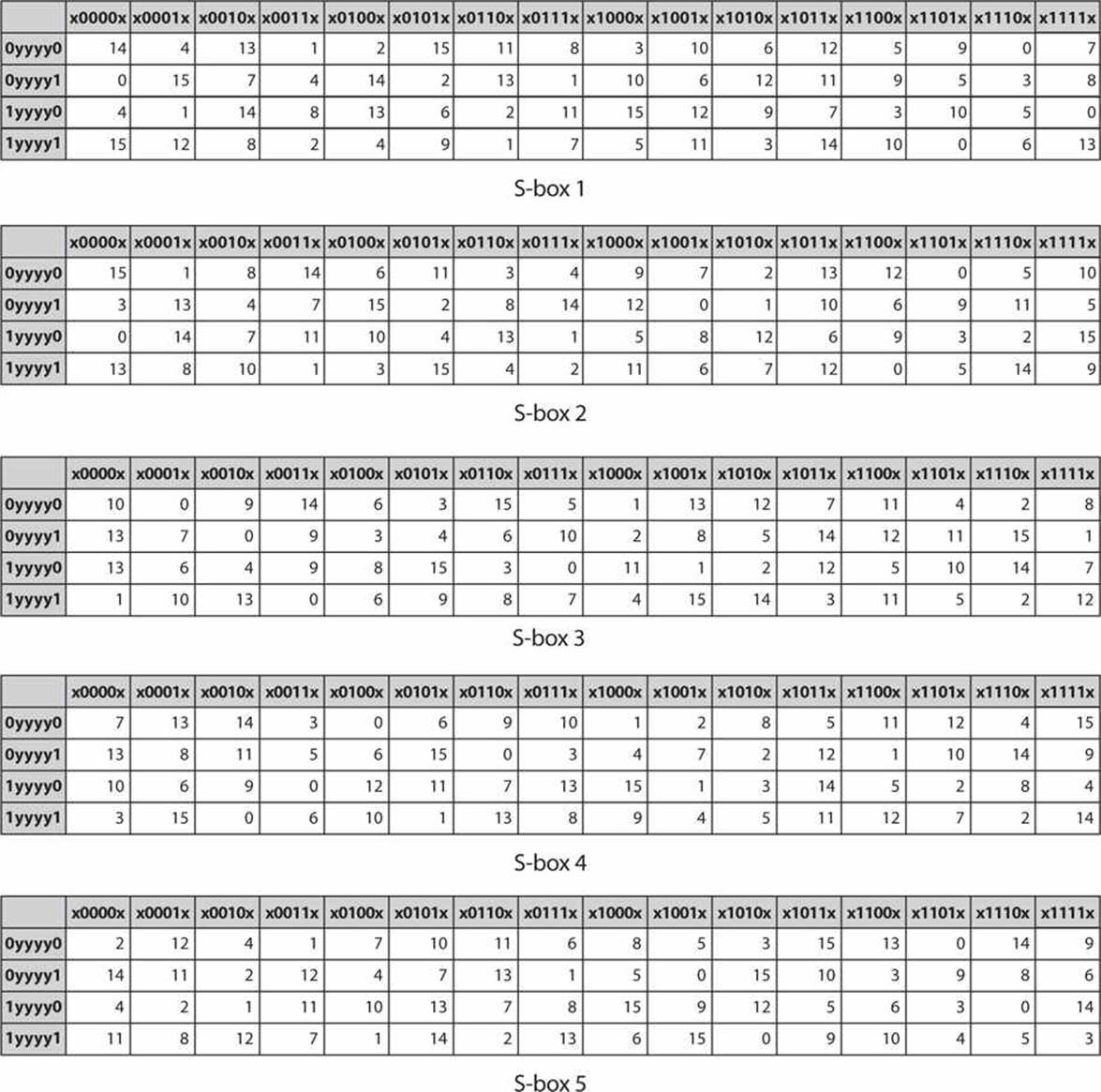
S-Box Design - Symmetric Ciphers and Hashes - Modern Cryptography: Applied Mathematics for Encryption and Informanion Security (2016)
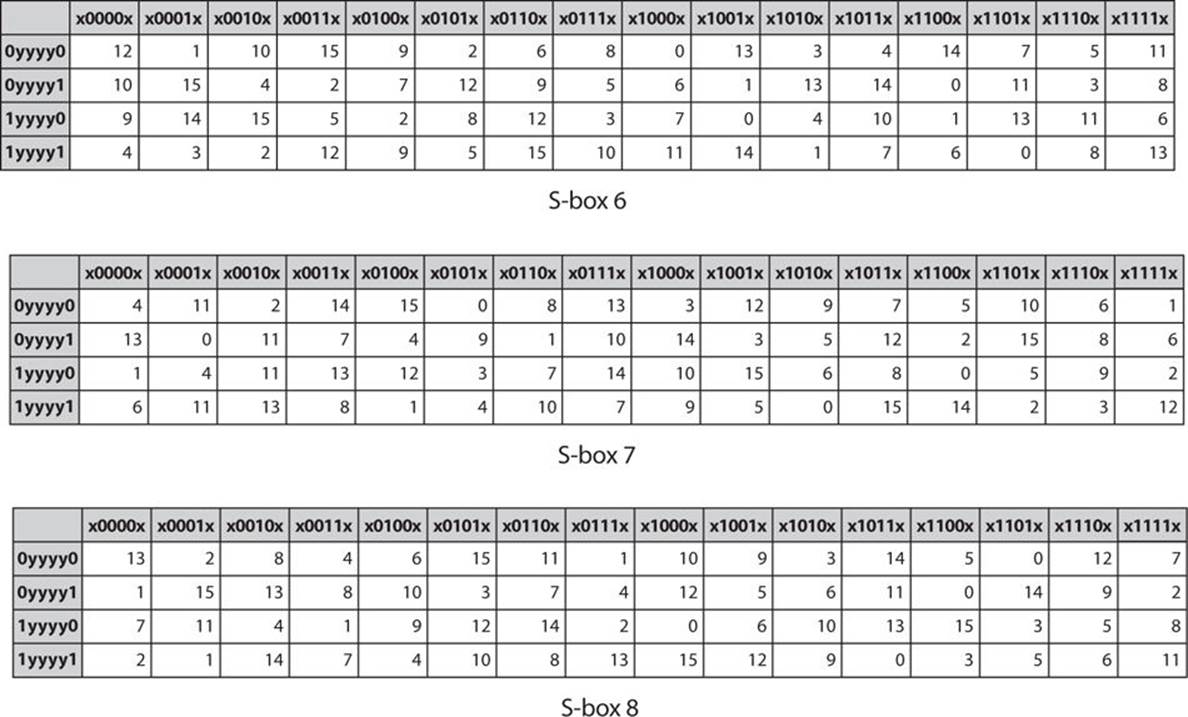
S-Box Design - Symmetric Ciphers and Hashes - Modern Cryptography: Applied Mathematics for Encryption and Informanion Security (2016)

ARIA — Why Have One S-Box, When You Can Have Two? | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium



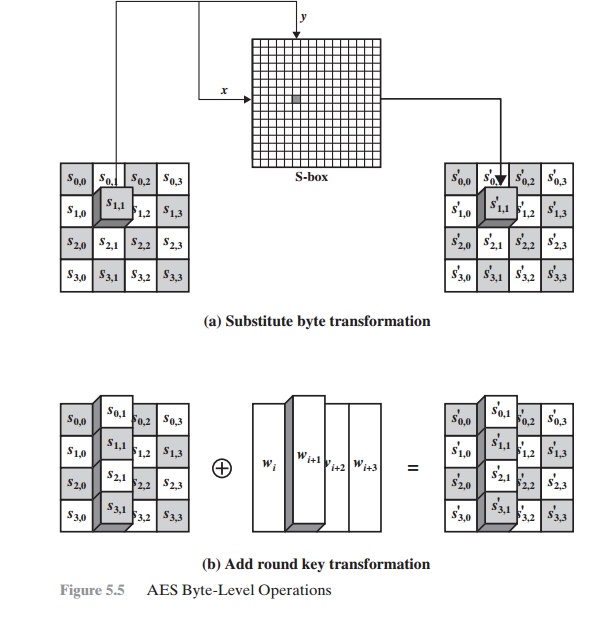
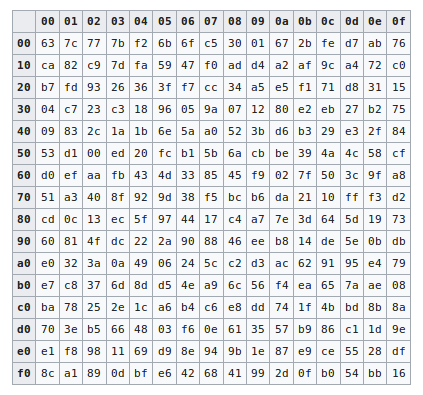
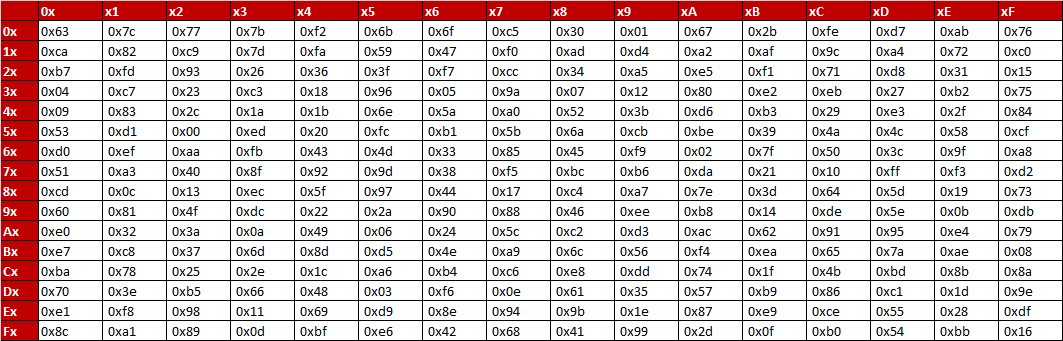
![PDF] AN IMPROVED AES S-BOX AND ITS PERFORMANCE ANALYSIS | Semantic Scholar PDF] AN IMPROVED AES S-BOX AND ITS PERFORMANCE ANALYSIS | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/af65a349981b8c3ef96c1f7725ba78c398aba27b/7-Table3-1.png)




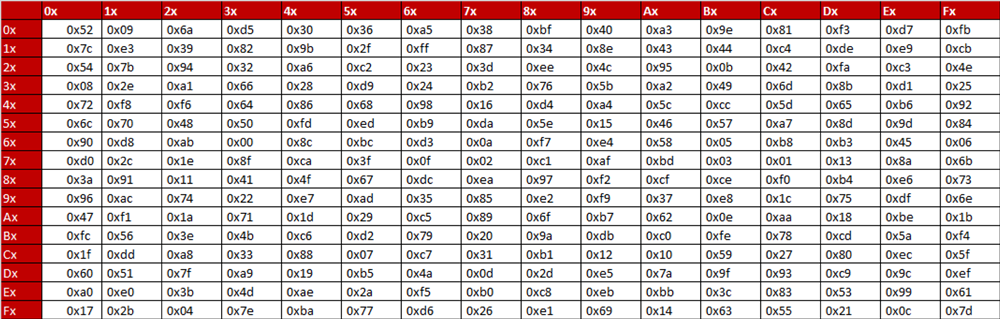
![PDF] Key-Dependent S-Box Generation in AES Block Cipher System | Semantic Scholar PDF] Key-Dependent S-Box Generation in AES Block Cipher System | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/dbb048954cea8033c4f51e7af535be17d9dacdf3/8-Table2-1.png)






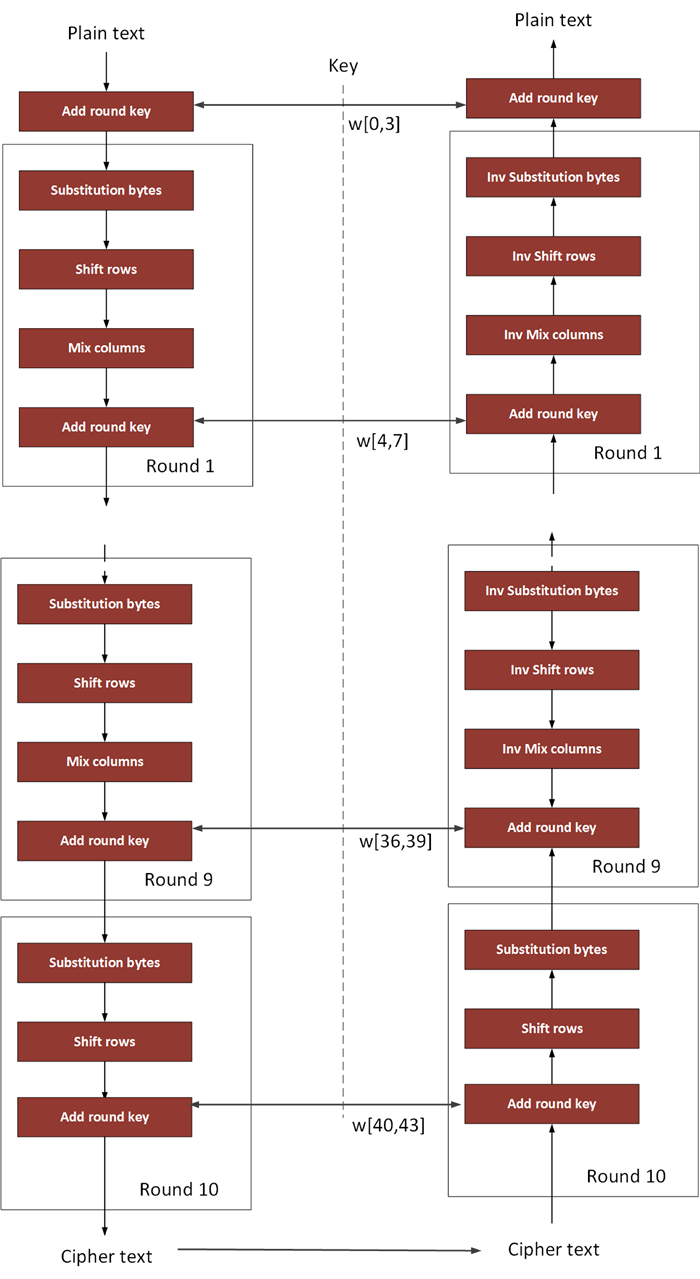

![PDF] Key-Dependent S-Box Generation in AES Block Cipher System | Semantic Scholar PDF] Key-Dependent S-Box Generation in AES Block Cipher System | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/dbb048954cea8033c4f51e7af535be17d9dacdf3/9-Table3-1.png)